Matter is a protocol designed with security and privacy in mind. Cryptography is widely adopted in Matter to ensure:
- Trusted devices
- Trusted controllers
- Private communication
In this post we will go through the Matter security model and investigate how these targets are accomplished in Matter.
Introduction to Public Key Infrastructure#
The Matter security model is based on Public Key Infrastructure(PKI), a cryptographic mechanism widely adopted in the Internet. When you visit a website via https, the connection is secured by the site’s certificate.
Here is the certificate chain of www.espressif.com:
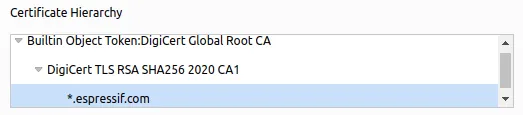
The certificate chain is hierarchical structure. Each certificate in the chain is signed by its issuer, tracing back to the root certificate. A site will be trusted if its certificate can trace back to one of the trusted root certificates stored in the browser.
The PKI works together with session establishment protocols to achieve some key cryptograpic goals:
- Identification : The peer’s identification will be verified by the signature of its issuer.
- Data privacy & integrity : All communication will be encrypted by a unique key independently negotiated for each session.
In the following part of the aritcle, we’ll see how Matter facilites the PKI to achieve different security goals and how certificates are distributed among your apps and devices.
Certificates in Matter#
Device Attestation Certificate: Is the device what it claims to be?#
All matter devices will be shipped with a unique Device Attestation Certificate (DAC). This certificate guards you against fakes: You can say with confidence the device comes from the brand on its box. This device identity authentication comes from the certificate chain of the DAC.
The DAC is signed by the Product Attestation Intermediate (PAI) certificate. This certificate will be typically held by the device manufacturers. The PAI certificate in turn is signed by the Product Attestation Authority (PAA) certificate. This PAA certificate acts as the root CA and provides root of trust. The list of trusted PAA certificates are stored in the Distributed Compliance Ledger (DCL), a distributed storage provided by the Connectivity Standard Alliance. We’ll have an in-depth article about DCL in the following posts.
The DAC and the PAI is burnt to the persistent storage of the device during manufacturing. During the commissioning process, the controller will retrieve them and verify the certificates as well as the Vendor/Product information shipped with the certification. Such verification step guarantees that all commissioned Matter devices are trusted.
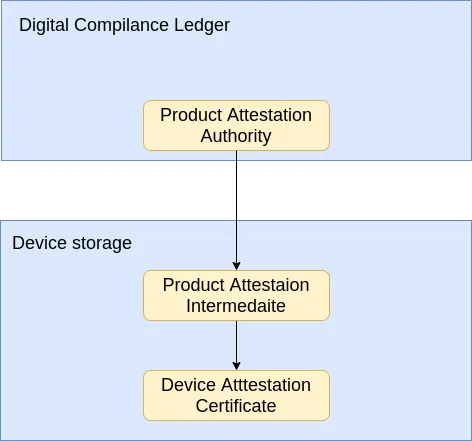
Node Operational Credentials: Who do I talk to?#
Public key certificates are also used to authenticate the peer and ensure data privacy and integrity in the Matter protocol. The key used in this scenario is the Node Operational Crendential (NOC).
The NOC can be signed by an Intermediate Certificate Authority (ICA) or be directly signed by the Root Certificate Authority (RCA). The RCA is typically generated by the commissioner. During the commissioning process, the NOC and the RCA are installed to the device.
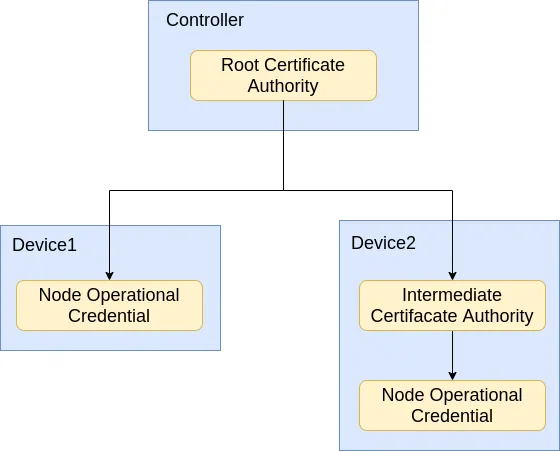
When the app or another device connects to the device, the certificate information will be exchanged. The devices will trust each other if they share the same root certificate. Devices with same root certficate thus form a Matter fabric . After the certificate information exchange, an encrypted session will be established between the peers.
Bringing it all together: Commissioning#
The device commissioning process configures an out-of-box device. It authenticates the device, sets up the network and installs the NOC to the device storage.
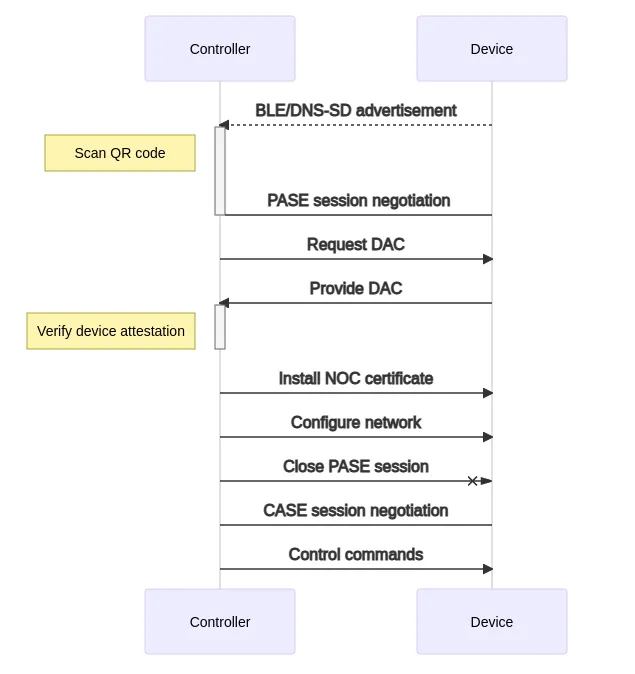
Once the device is powered, it will advertise itself via BLE advertisement or DNS-sd service advertisement. When the controller receives the advertisement, it will try to establish an encrypted session with the device based on the pairing code. This process is called Password Authenticated Session Establishment (PASE) in Matter. Typically the app will scan a QR code to retrieve the unique pairing code of the device, in the PASE process.
After setting up the PASE session, the controller will check the DAC of the device. Once the device attestation certificate is authenticated, a new NOC will be signed and installed to the device. The controller will also tell the device about the Wi-Fi or the Thread network to join. Once the device has been correctly configured, the PASE session will be closed. All the following communications will be based on the certificate. The new session is called Certificate Authenticated Session Establishment (CASE) in Matter.
In a CASE session, the peers exchange their certificate information with salts to authenticate each other and negotiate a credential for symmetric encryption. All the control commands are protocted with this negotiated key.
The following diagram contains a typical flow for pairing a Matter device out-of-the-box.
That summarises how PKI forms an integral part of the Matter specification.
This article is a part of a series of articles Espressif Matter Series.


