Overview#
The “software bill of materials” (SBOM) has emerged as a key building block in software security and software supply chain risk management. An SBOM is a comprehensive list of all the software components, dependencies, and metadata associated with an application.
Espressif believes that this information is a key step towards ensuring the security of the connected devices. And as such, we have now enabled easy to use tools and solutions to track and analyze this information.
In this blog post, we shall look through the Espressif’s SBOM generator and analysis tool, ESP-IDF-SBOM .
SBOM#
According to National Telecommunications and Information Administration’s (NTIA) SBOM FAQ, the official definition of SBOM goes as follows:
A Software Bill of Materials (SBOM) is a complete, formally structured list of components, libraries, and modules that are required to build (i.e., compile and link) a given piece of software and the supply chain relationships between them. These components can be open source or proprietary, free or paid, and widely available or restricted access.
Key data fields for each component includes:
- Supplier Name
- Component Name
- Version of the Component
- Other Unique Identifiers
- Dependency Relationship
- Author of SBOM Data
- Timestamp
SBOM data needs to be presented in consistent and digestible formats. Some formats to handle the data representation are SPDX, CycloneDX etc.
Simple conceptual SBOM tree for wifi_provisioning component from ESP-IDF looks like below:
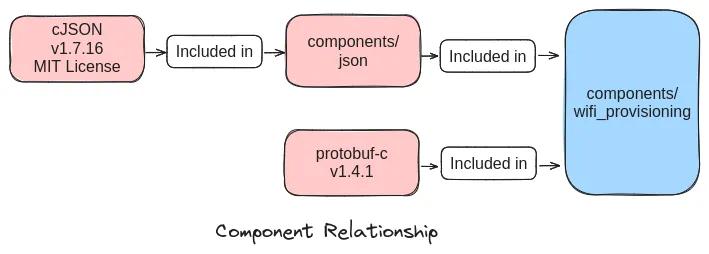
SPDX#
Software Package Data Exchange (SPDX) is an open standard for communicating software bill of materials (SBOM) information that supports accurate identification of software components, explicit mapping of relationships between components, and the association of security and licensing information with each component.
The image below outlines what data can be found in an SPDX document.
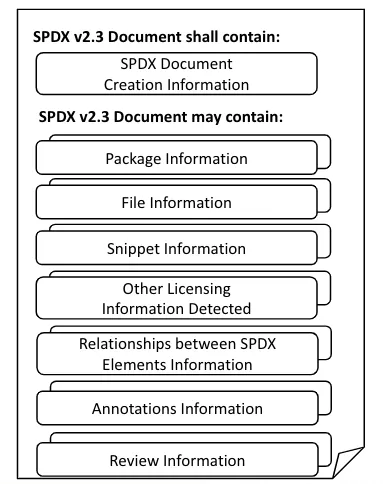
ESP-IDF-SBOM#
ESP-IDF-SBOM is a SBOM generator tool. It generates SPDX format SBOM for ESP-IDF based applications. This tool also allows to check the generated SBOM for known security vulnerabilities against National Vulnerabilitiy Database (NVD).
SBOM Generator Workflow#
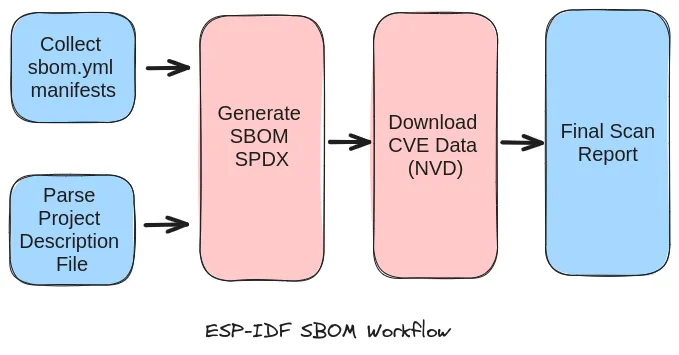
Brief tool workflow goes like:
- Collect sbom.yml (a manifest file) files from dependant components
- Parse project description file generated by the ESP-IDF build system
- Generate SPDX report
- Scan generated SPDX against the CVE databse to generate final report
Getting Started#
Install the tool and checkout its help:
$ pip install esp-idf-sbom
$ esp-idf-sbom --help
usage: esp-idf-sbom [-h] [-q] [-n] [-f] [-v] [-d] [--no-progress] {create,check,manifest} ...
ESP-IDF SBOM tool
positional arguments:
{create,check,manifest}
sub-command help
create Create SBOM file based on the ESP-IDF project_description.json file.
check Check components/submodules in the ESP-IDF SBOM file for possible
vulnerabilities reported in the National Vulnerability Database.
manifest Commands operating atop of manifest files.
options:
-h, --help show this help message and exit
-q, --quiet By default auxiliary messages like errors, warnings, debug messages
or progress are reported to the standard error stream. With this
option set, all such messages are suppressed.
-n, --no-colors Do not emit color codes. By default color codes are used when stdout
or stderr is connected to a terminal.
-f, --force-colors Emit color codes even when stdout or stderr is not connected to a
terminal.
-v, --verbose Be verbose. Messages are printed to standard error output.
-d, --debug Print debug information. Messages are printed to standard error
output.
--no-progress Disable progress bar.
Generate the SBOM file:
$ cd esp-idf/examples/provisioning/wifi_prov_mgr
$ idf.py build
$ esp-idf-sbom create <project description file> --output-file prj.spdx
The project description file is a path to the project_description.json file, which is by default created by the ESP-IDF build system in the project’s build directory.
Check SBOM against the security vulnerabilities:
$ esp-idf-sbom check prj.spdx
Report summary
┌───────────────────────────────────┬─────────────────────────────────────────────────────────┐
│ Date: │ 2023-10-10T08:21:39Z │
│ Project name: │ project-wifi_prov_mgr │
│ Project version: │ v5.2-dev-3250-g7d8f015a4c │
│ Vulnerability database: │ NATIONAL VULNERABILITY DATABASE (https://nvd.nist.gov) │
│ Generated by tool: │ esp-idf-sbom (0.8.0) │
│ Generated with command: │ esp-idf-sbom check prj.spdx │
│ Number of scanned packages: │ 57 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ CRITICAL CVEs found: │ │
│ Packages affect by CRITICAL CVEs: │ │
│ Number of CRITICAL CVEs: │ 0 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ HIGH CVEs found: │ │
│ Packages affect by HIGH CVEs: │ │
│ Number of HIGH CVEs: │ 0 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ MEDIUM CVEs found: │ │
│ Packages affect by MEDIUM CVEs: │ │
│ Number of MEDIUM CVEs: │ 0 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ LOW CVEs found: │ │
│ Packages affect by LOW CVEs: │ │
│ Number of LOW CVEs: │ 0 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ UNKNOWN CVEs found: │ │
│ Packages affect by UNKNOWN CVEs: │ │
│ Number of UNKNOWN CVEs: │ 0 │
├───────────────────────────────────┼─────────────────────────────────────────────────────────┤
│ All CVEs found: │ │
│ All packages affect by CVEs: │ │
│ Total number of CVEs: │ 0 │
└───────────────────────────────────┴─────────────────────────────────────────────────────────┘
Packages with No Identified Vulnerabilities
┏━━━━━━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━┳━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┓
┃ Package ┃ Version ┃ CPE ┃
┡━━━━━━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━╇━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━┩
│ project-wifi_prov_mgr │ v5.2-dev-3250-g7d8f015a4c │ cpe:2.3🅰️espressif:esp-idf:5.2-dev-325 │
│ │ │ 0-g7d8f015a4c:*:*:*:*:*:*:* │
├───────────────────────┼───────────────────────────┼─────────────────────────────────────────┤
│ lwip │ 2.1.3 │ cpe:2.3🅰️lwip_project:lwip:2.1.3:*:*:* │
│ │ │ :*:*:*:* │
├───────────────────────┼───────────────────────────┼─────────────────────────────────────────┤
│ cjson │ 1.7.16 │ cpe:2.3🅰️cjson_project:cjson:1.7.16:*: │
│ │ │ *:*:*:*:*:* │
├───────────────────────┼───────────────────────────┼─────────────────────────────────────────┤
│ protobuf-c │ 1.4.1 │ cpe:2.3🅰️protobuf-c_project:protobuf-c │
│ │ │ :1.4.1:*:*:*:*:*:*:* │
├───────────────────────┼───────────────────────────┼─────────────────────────────────────────┤
│ mbed_tls │ 3.4.1 │ cpe:2.3🅰️arm:mbed_tls:3.4.1:*:*:*:*:*: │
│ │ │ *:* │
├───────────────────────┼───────────────────────────┼─────────────────────────────────────────┤
│ freertos │ 10.4.3 │ cpe:2.3⭕amazon:freertos:10.4.3:*:*:*: │
│ │ │ *:*:*:* │
└───────────────────────┴───────────────────────────┴─────────────────────────────────────────┘
...snip
Some highlights from the SBOM vulnerability check:
- wifi_prov_mgr application from ESP-IDF v5.2-dev was used for the exercise
- It is possible to scan the components which are not linked into final executable by adding –check-all-packages in the check command shown above
- It is also possible to generate the SBOM report for the ESP-IDF bootloader. Bootloader specific build description file can be found in the build/bootloader directory inside the project
- Some key components like RTOS, Networking Stack, TLS Stack etc. having Common Platform Enumeration entries have been highlighted in the above output
- Tool also displays information about other component and libraries (not shown in the above log) which are part of the build process
Report Format#
This tool supports multiple formats for the generated output report like JSON, CSV etc. Please refer to the tool help for more details.
Compatibility#
SPDX being a standard format for SBOM, also offers compatibility with the external tools. SBOM files generated from esp-idf-sbom can also be scanned using tools like cve-bin-tool. This offers an added advantage if you already have any external tools integrated in your system and want to take advantage of its specific features (e.g., more extended scan against different CVE databases).
Summary#
To summarize, some key advantages of SBOM are:
- Forms inventory of the components building the software artifacts
- Lists software licenses, component versions and helps to keep them up-to-date
- Helps to perform security vulnerability analysis
- Becoming a pre-requisite in many security related certifications
ESP-IDF-SBOM tool is useful to generate SBOM for ESP-IDF based projects. The tool can also further help to scan and setup process for continuous security vulnerability scanning of the project.
We are actively working on to enable wider SBOM coverage across our software solutions and looking for feedback on the ESP-IDF-SBOM tool.
Please do try and share your experience!



